Authentication on
Application Load Balancer
 ALB Auth
ALB Auth
This site has the 'Authenticate' action on every rule with the 'allow' setting for unauthenticated requests. This means every request that is authenticated will include the information of that user from the OIDC provider. It has a rule for the path '/auth' with 'Authenticate' on it and 'authenticate' as the action for unauthenticated users. The server code is a simple application which looks for the 'X-Amzn-Oidc-Data' HTTP header, which is included by the ALB. It extracts that info, verifies the signature, and includes it in response processing. This site doesn't do anything beyond check if you're logged in or not and then display the keys and their values contained in the data.
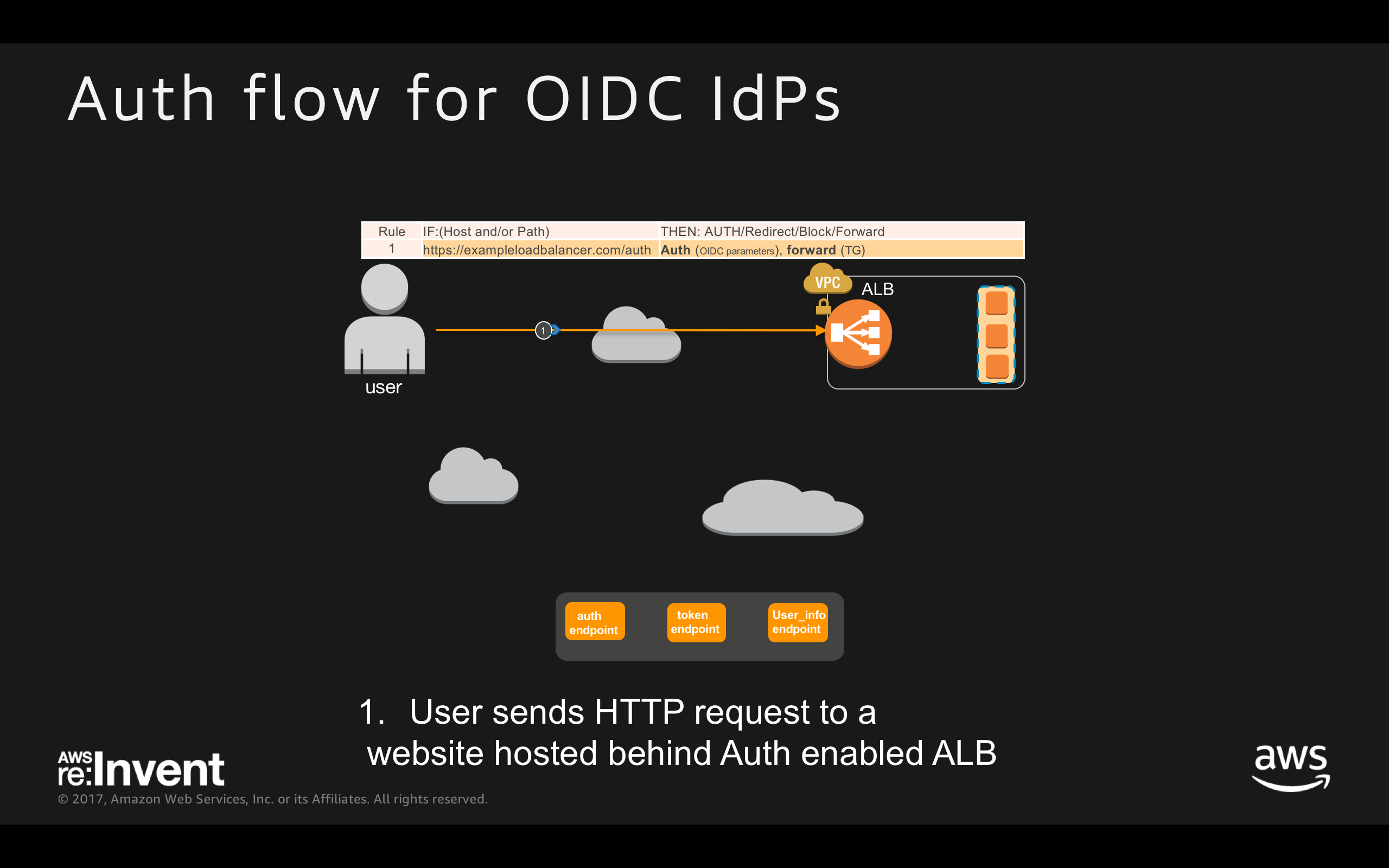
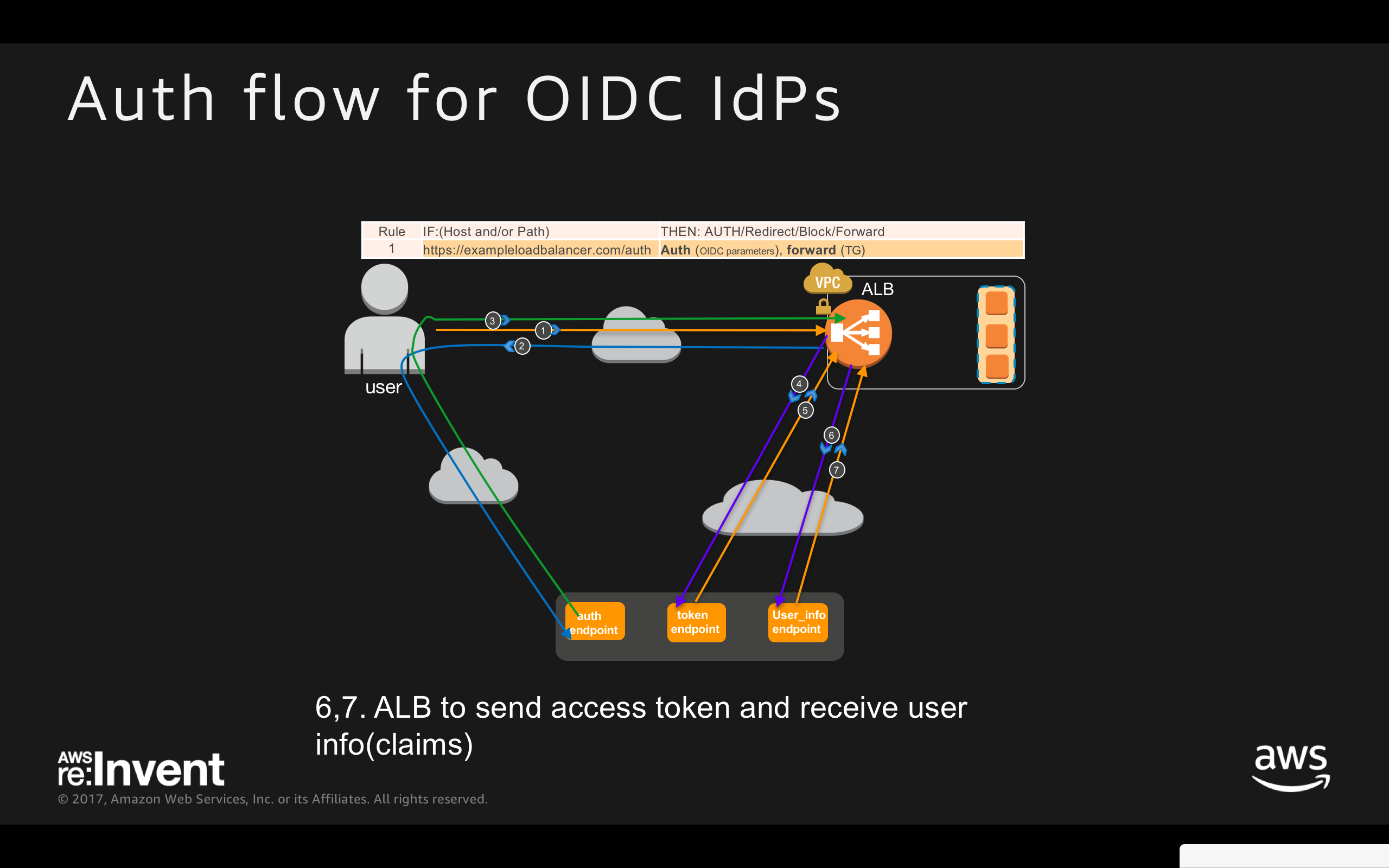
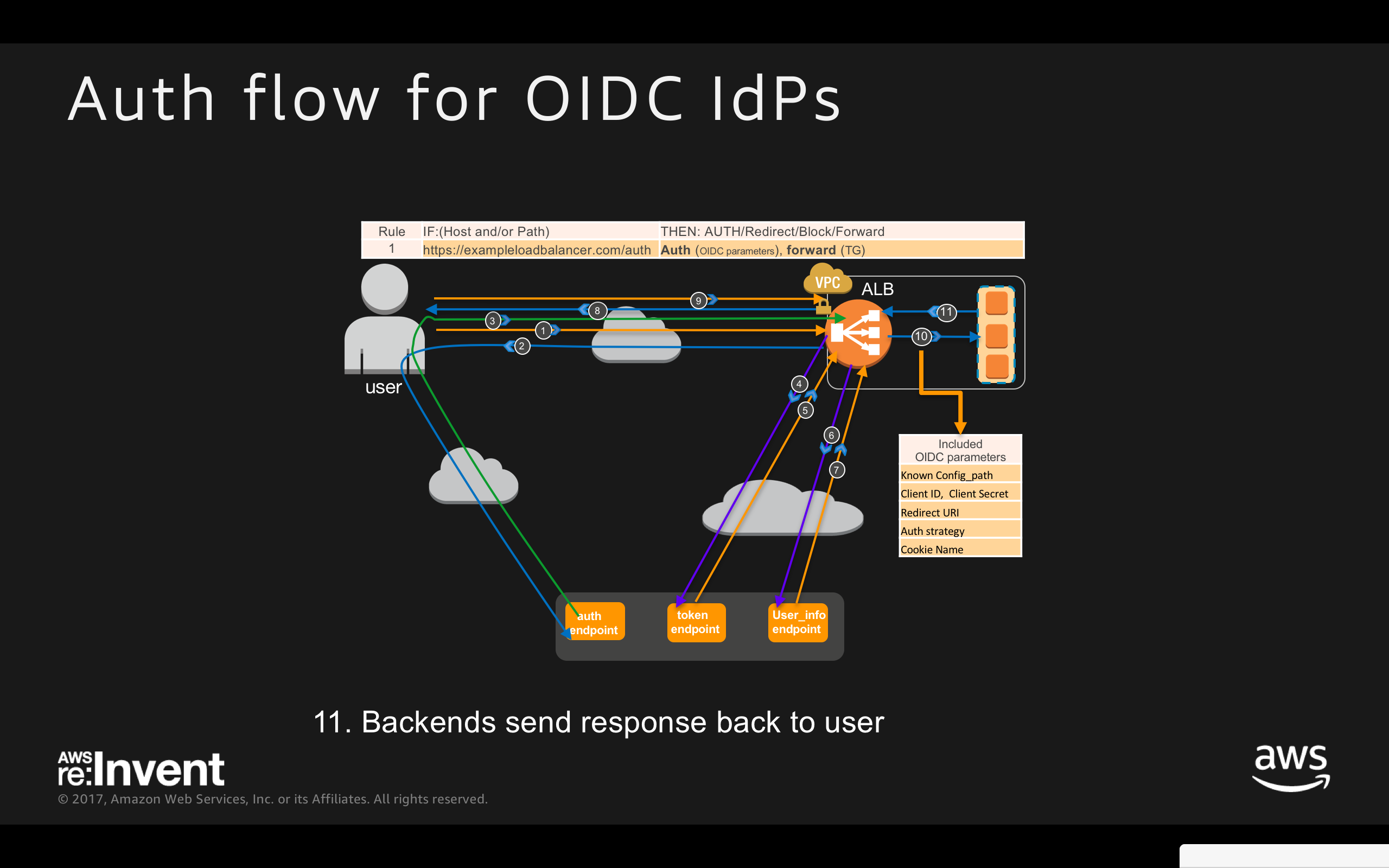
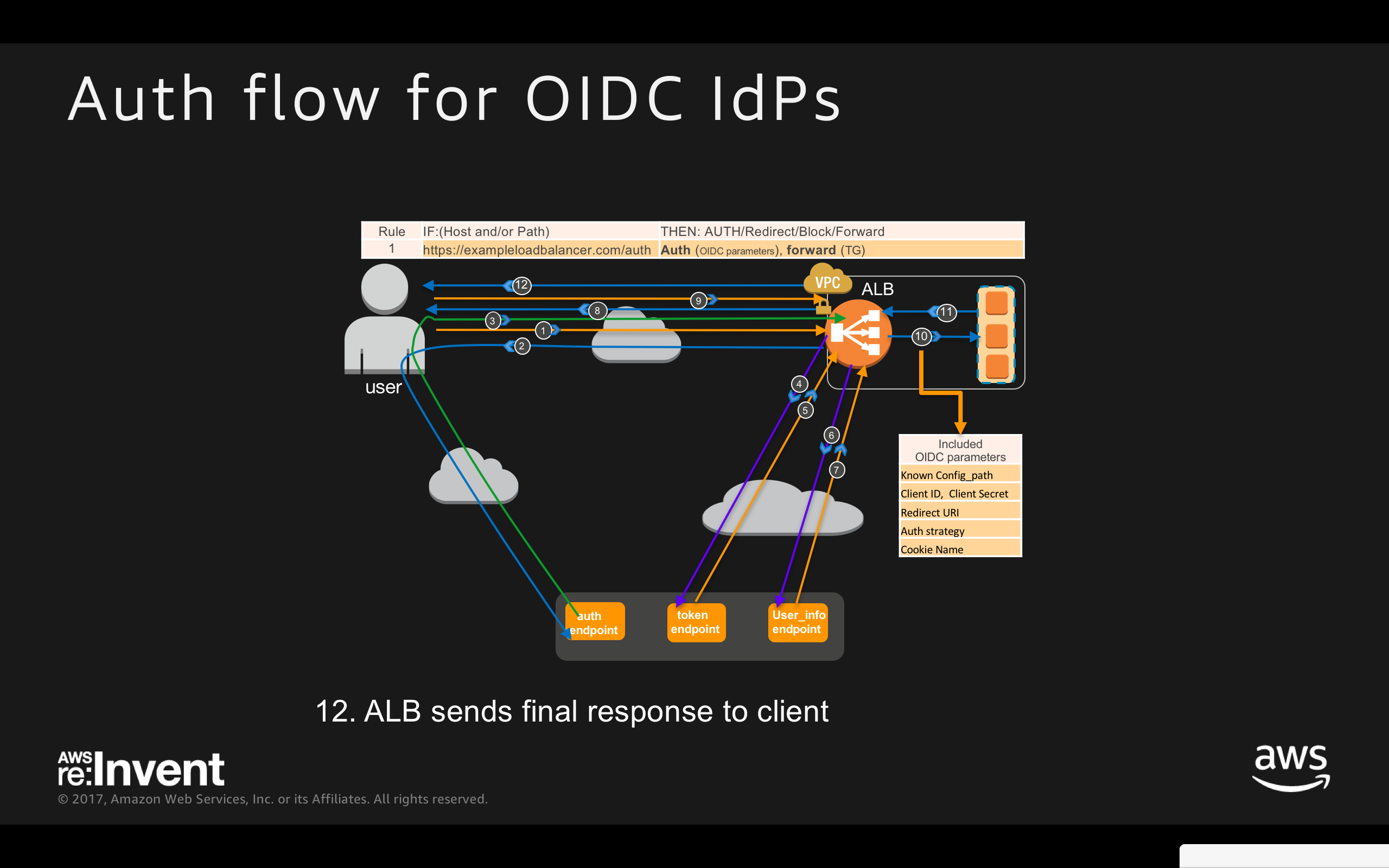
ALB Authentication Workflow for OIDC IdPs:
- User sends HTTP request to a website hosted behind Auth enabled ALB
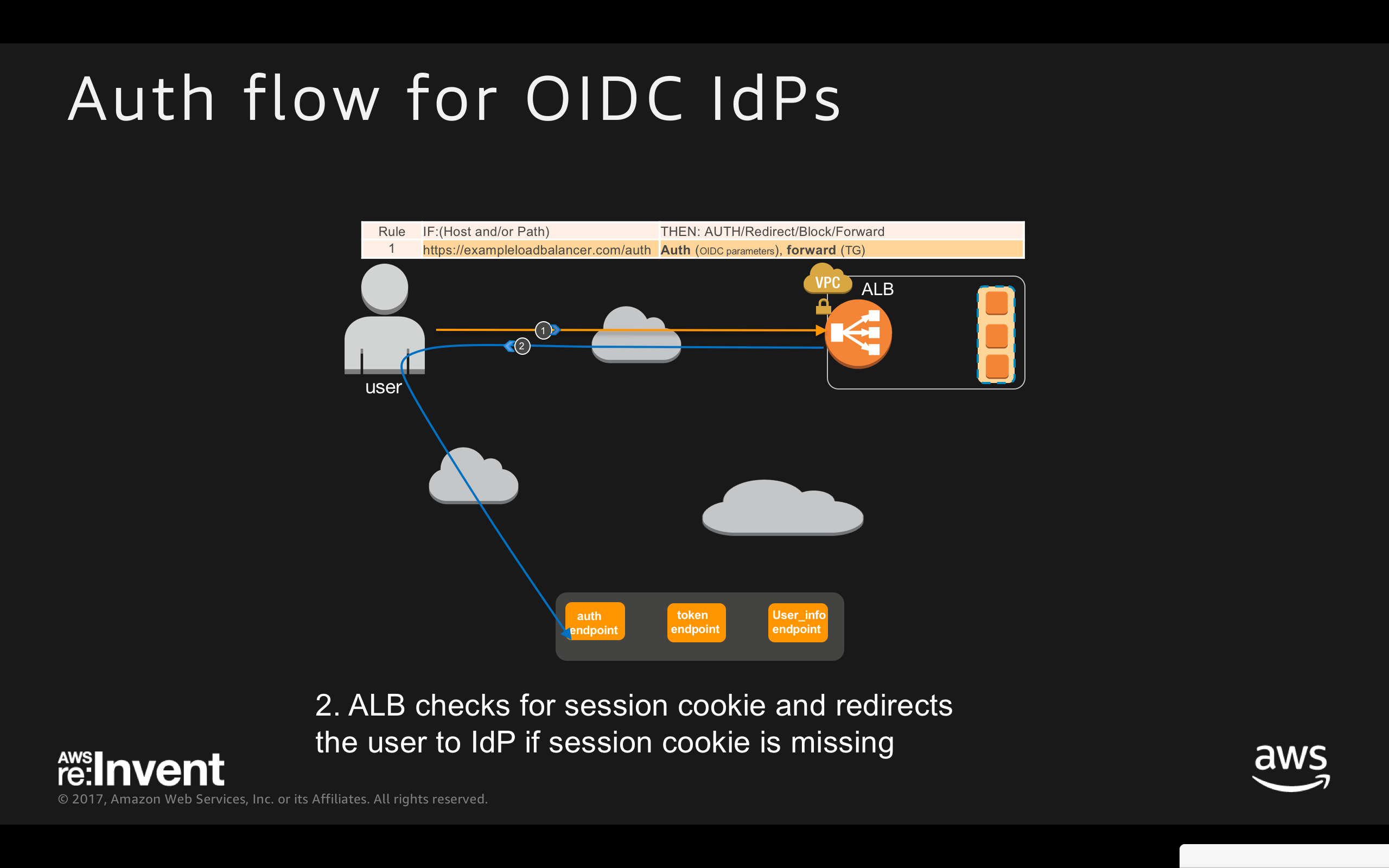
- ALB checks for session cookie and redirects the user to IdP if session cookie is missing
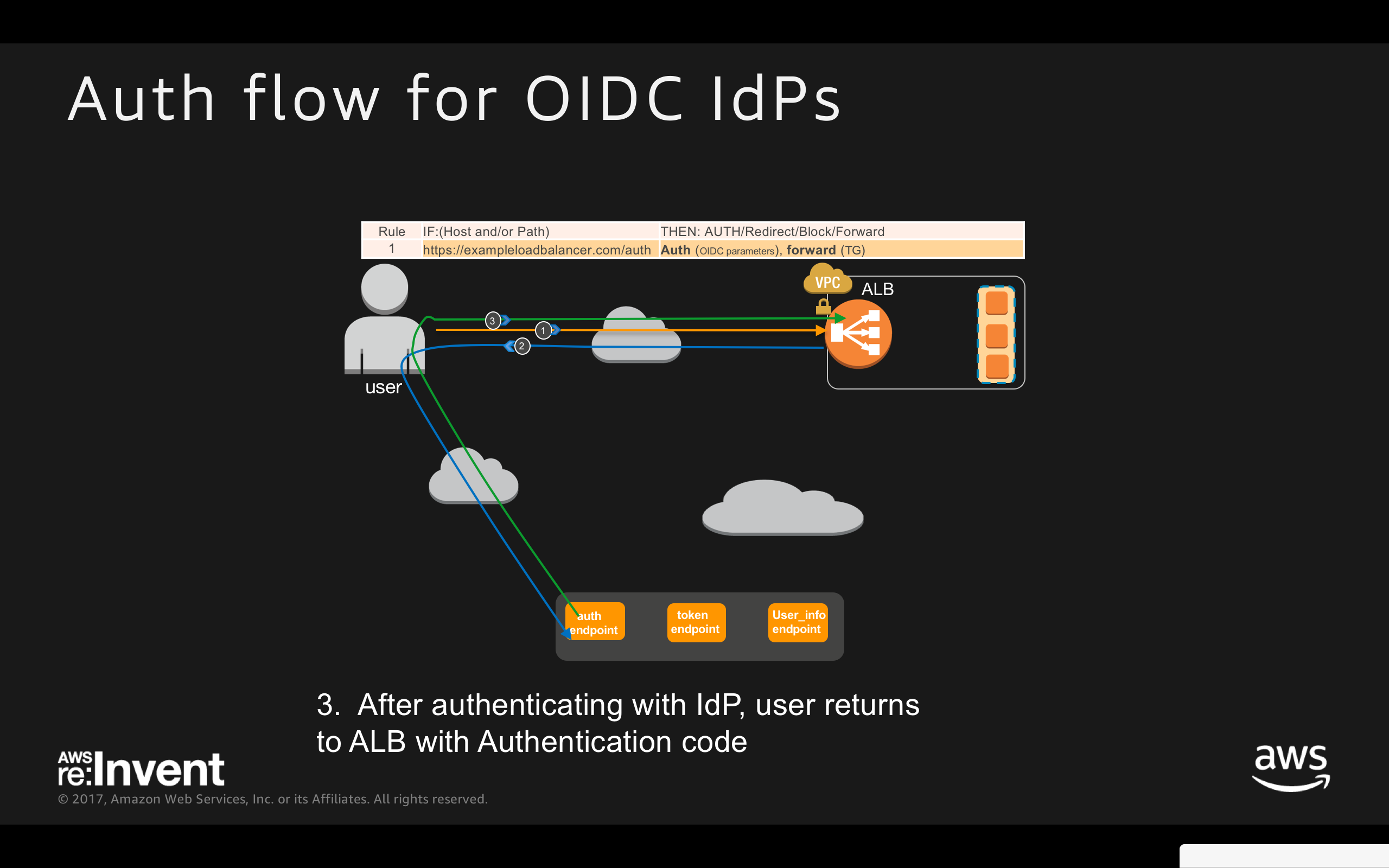
- After authenticating with IdP, user returns to ALB with Authentication CODE
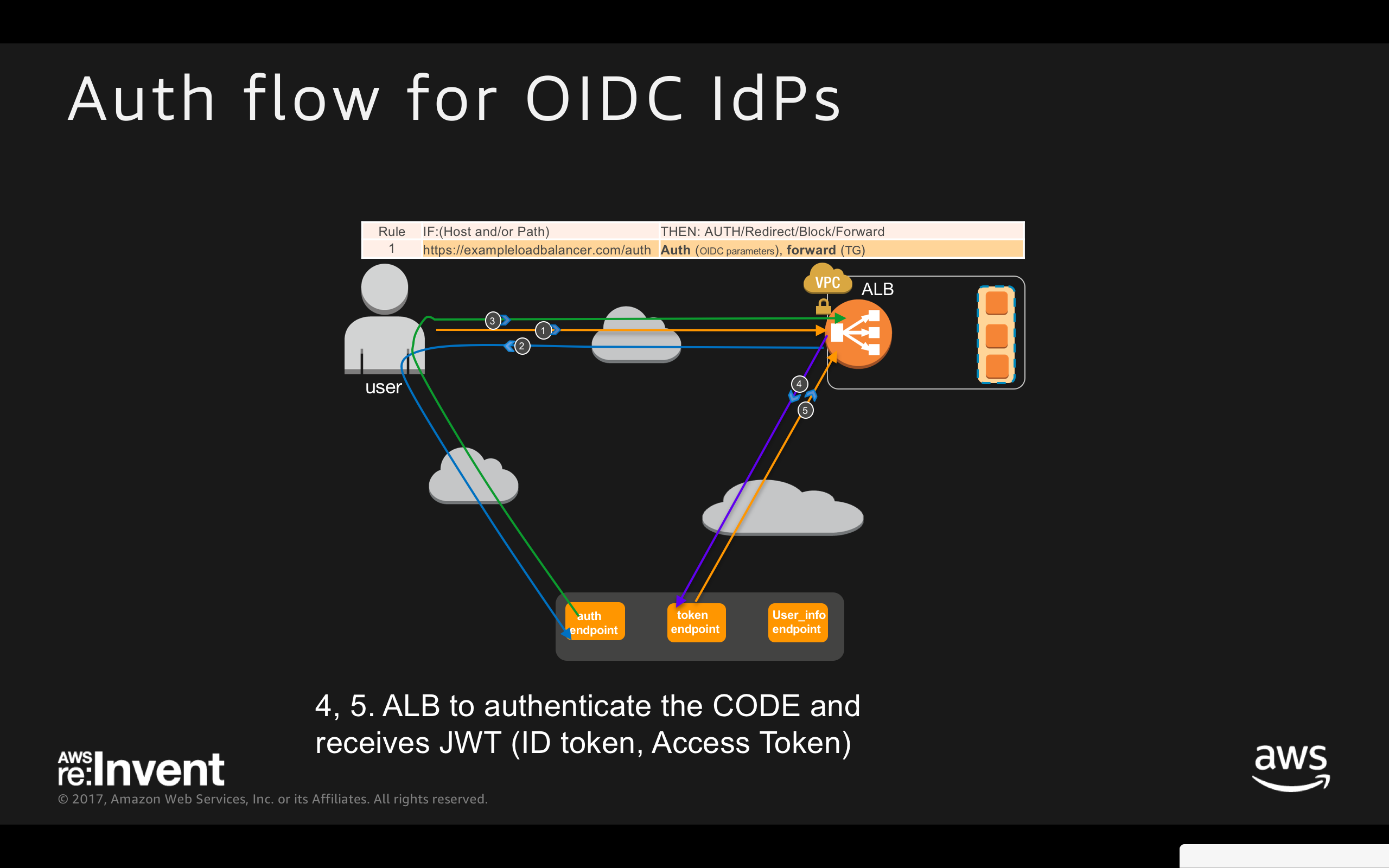
- ALB to authenticate the CODE
- ALB receives JWT (ID token, Access Token)
- ALB to send access token
- ALB receives user info(claims)
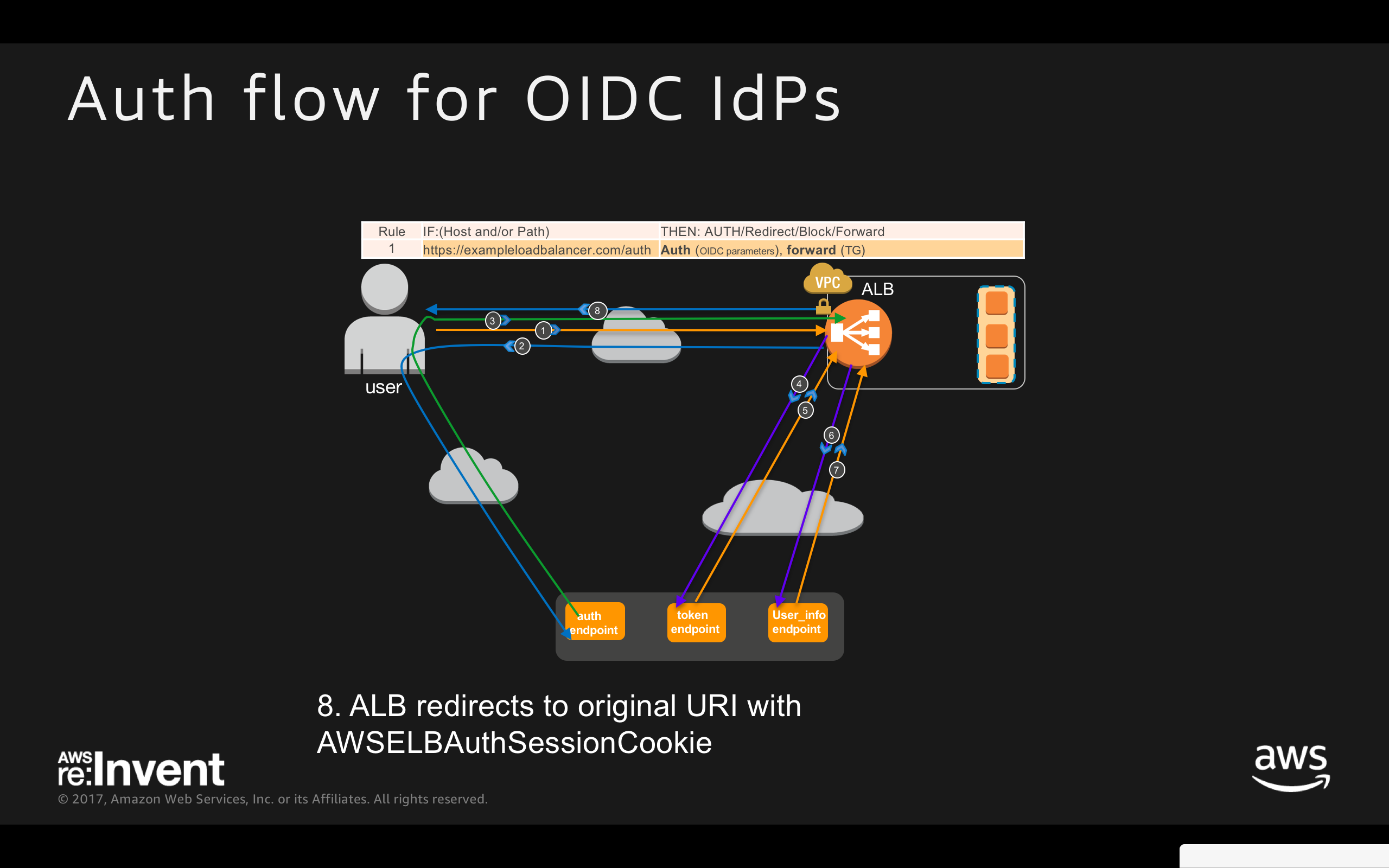
- ALB redirects to original URI with AWSELBAuthSessionCookie
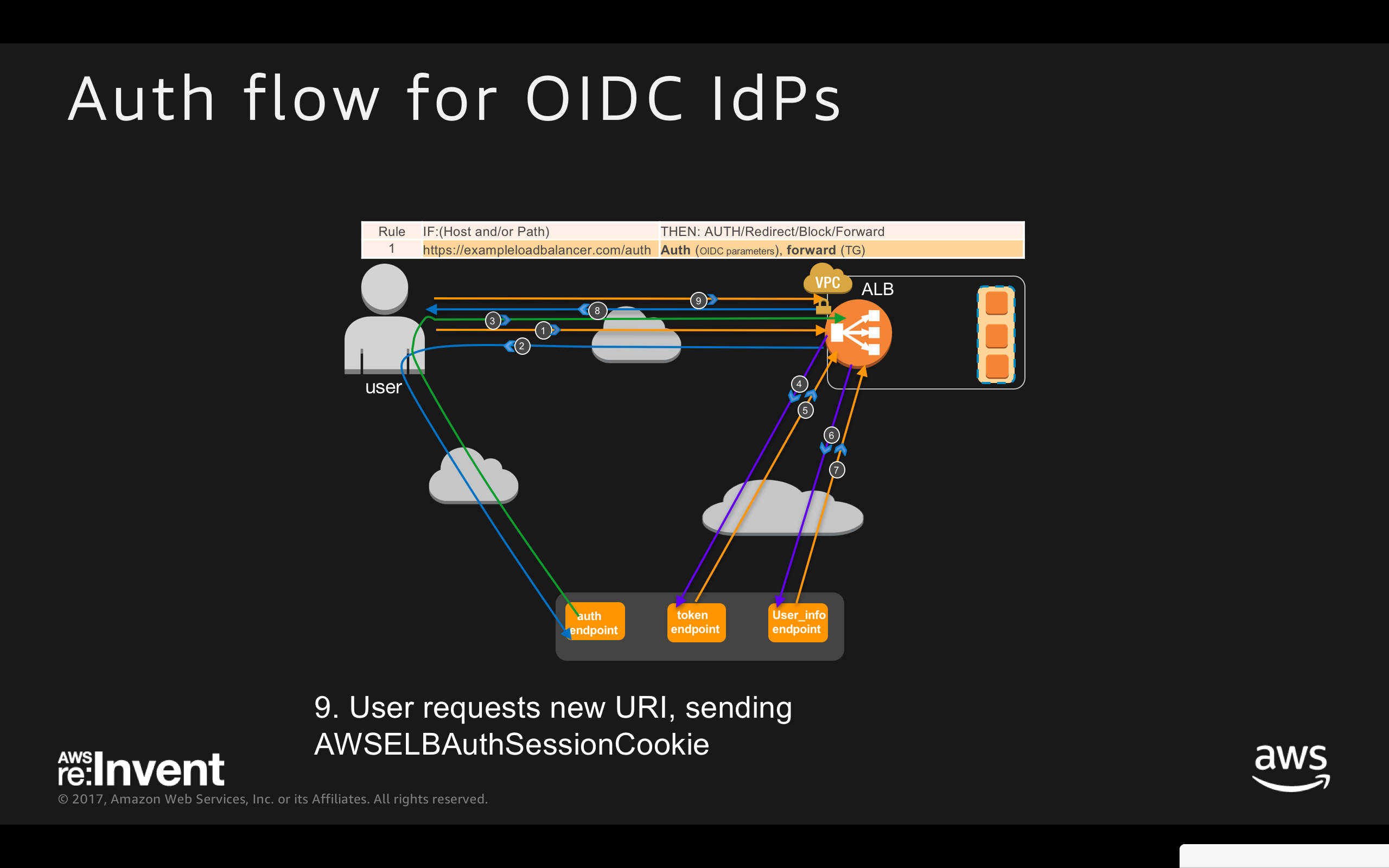
- User requests new URI with AWSELBAuthSessionCookie
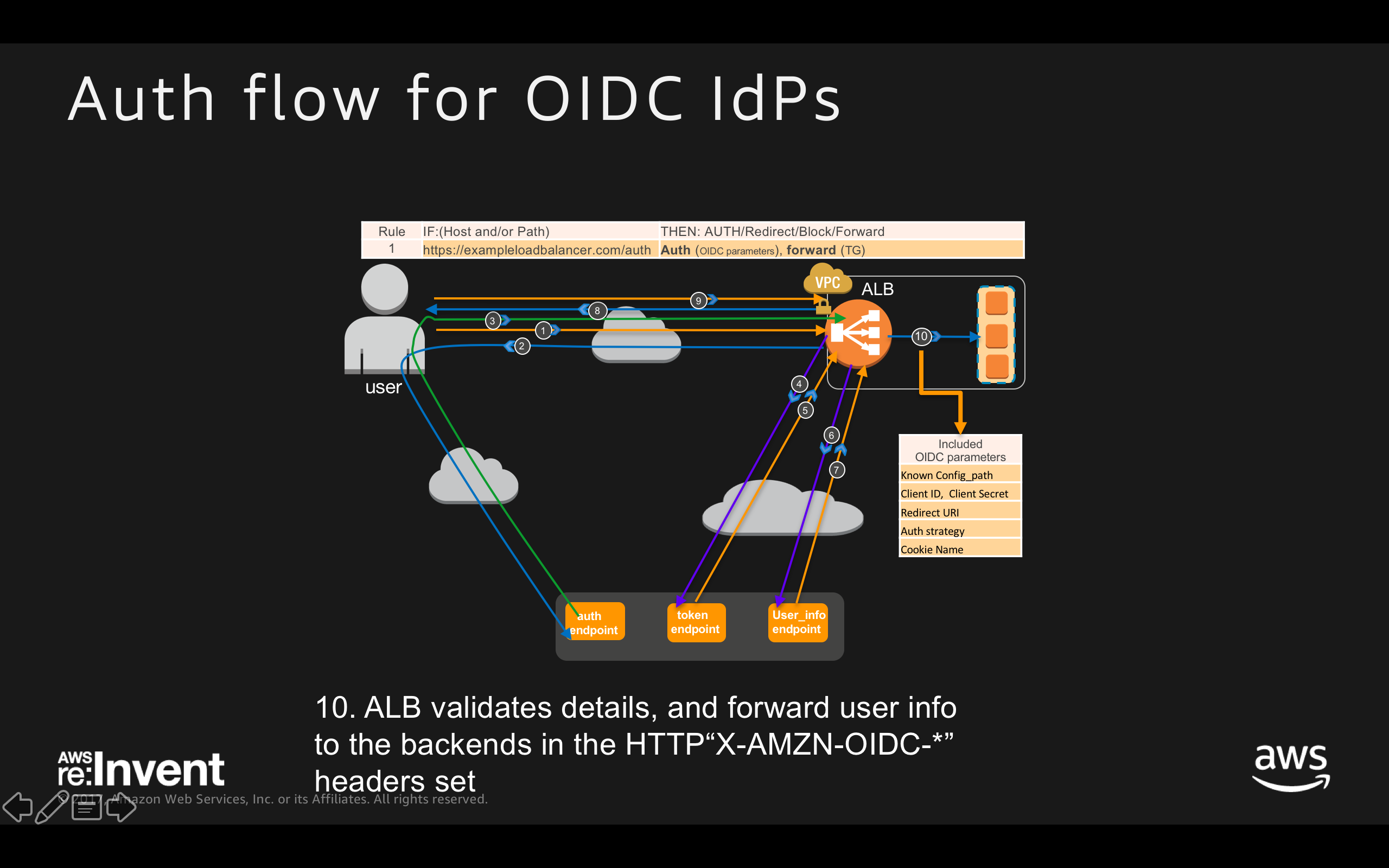
- ALB validates details, and forward user info to the backends in the HTTP“X-AMZN-OIDC-*” headers set
- Backends send response back to the user
- ALB sends final response to client
Resources:
We also have cats

Blog Post
Read the Blog Post from the launch of Authentication on Application Load Balancer